How to Prevent Hackers from Accessing Your Mail and Other Online Services
Online security is more relevant than ever. News from hackers breaching massive number of user accounts from an online service no longer surprises anyone.
Two important things that you should do today to improve the security of your online accounts are setting up two-factor authentication and using a password manager.
Two-factor Authentication
Two-factor authentication means that each time you log into an online service, before you can get access to your account, you’ll be asked to enter an additional code after you enter your password. This code is generated by an app on your phone1, or sent to you by SMS, and changes every 30 seconds. With two-factor authentication enabled, even if your password is compromised, a hacker cannot log in into your account.
Ideally, security is based on three things: something you know, something you have, and something you are. Almost everybody uses usernames and passwords. That’s something you know. But as security experts point out, “passwords have outlived their usefulness as a serious security device”. Adding something you have to the login process, like an additional code generated by an app in your phone, greatly enhances security.
If you are required to use your fingerprint to unlock your phone, then you’ve introduced a third factor: something you are. This is probably the best scenario you can get without resorting to professional-level security.

There are several authenticator apps on the market, perhaps the most well-known are Google Authenticator and Authy. Microsoft also offers an app. My personal favorite is Authy, because it syncs across devices so you can generate tokens from your phone or laptop. (Authy’s webpage offers a handful of guides on how to activate two-factor authentication on popular services. Check, for example, their guide for Gmail.)
What if your mail service provider doesn’t offer two-factor authentication? Don’t hesitate, change to a provider that does.
Use a Password Manager
The second most important thing is to use a password manager. Writing down your passwords on a stick-it note or in your iPhone’s Notes app is not only inefficient but insecure.
Companies that require their employees to change their passwords every 30 days, and don’t provide them with a password manager, are simply encouraging their employees to use weak, easy to guess passwords, or to write them down in a note they stick to their laptops.
With a password manager, you only need to remember one password: the one for the password manager itself. The app takes care of storing the usernames and passwords for every online service you use. Thanks to browser extensions, they recognize which webpage you are visiting and fill in the proper credentials. It also keeps you passwords synchronized between devices. (And yes, you can enable two-factor authentication for the password manager itself.)
Passwords and hashes
To understand why password length and complexity is important, we need to dive into how online services store passwords, and what hackers do when they steal user’s credentials from a server.
When an online service asks you to enter a password to create your account, the password is not stored as-is in the company’s servers. Instead, the server generates a hash code for the password. This hash code, and not the actual password, is stored along with your username and other data on the server2.
A hash is a mathematical function that takes a string of data as an argument, and produces a fixed-size series of numbers, which is call a hash code. Different passwords will produce different hash codes, and it is nearly impossible to deduce the original password from the hash code.
To verify your identity, the online service asks for your password, generates a hash code for the characters you typed in, and compares it to the hash code it generated when you created your account (or last changed your password). If both hash codes are equal, it means that the password you just typed and the password registered on the server are the same. You are granted access to your account.
Now and then, hackers break into an online service’s servers and steal data: email addresses, and password hashes, among other data. These stolen databases are sold in the black market for money3.
As computer processing power becomes cheaper, it is possible to try a brute-force attack against a stolen database and succesfully recover part of the original passwords from the hash codes. Brute-force means that the hacker will use a program to generate, systematically, passwords with every combination of characters, and compare their hash codes with the hash codes in the stolen database4. For every match, the attacker now knows he or she’s got the password for a given account.
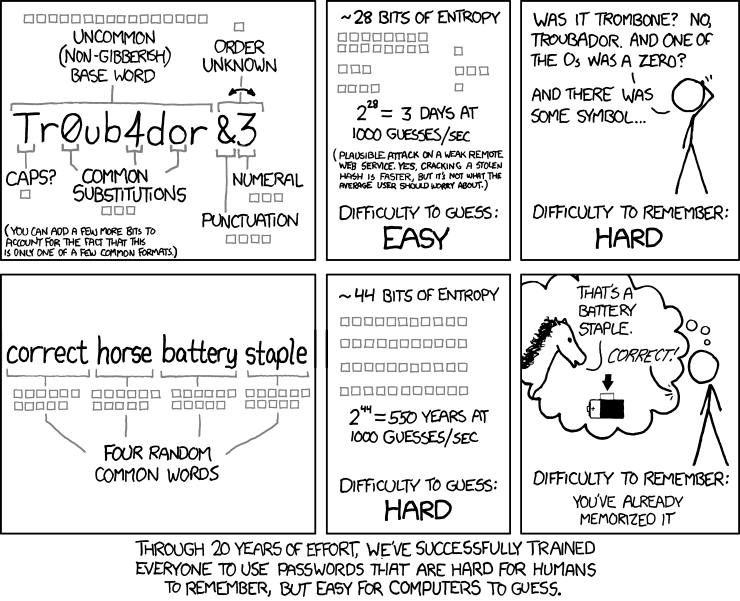
To protect you from this kind of attack, password managers allow you to generate long and random passwords for each new service you sign in. If you are inventing passwords by yourself, then your passwords are probably not long or complex enough. A long enough password ensures that a hacker won’t be able to crack it for several years from today.
This comic by xkcd’s Randall Munroe illustrates the point.
If the hacker get’s to know your username and password, chances are he or she will try to use them to access your accounts on popular services: Gmail, Facebook, Dropbox, Instagram, LinkedIn, etc. Once he’s got access to your email, he can request a password reset from other services, which will send a link to for resetting your password to your now-compromised email account. (That’s another reason to enable two-factor authentication.)
Which password manager should you use? I can recommend 1Password, which I’ve been using for several years now. Also, LastPass has excellent reviews.
Two-factor authentication and using a password manager are the most important things you should do today to improve online safety and protect your accounts from being hacked.
Photo by Dayne Topkin on Unsplash
These apps are called, among other names, two-factor authentication or 2FA apps, authenticator apps, one-time password or OTP apps. ↩
There are some online services that store their customer’s passwords as-is, which is a terrible practice. You can detect such services when you forget your password and click on the ‘Forgot your password?’ link: they’ll send you your password by email, instead of generating a new one or sending a link to reset it. ↩
There are pages that will tell you if your email has been compromised in a data breach. Check, for example, \. ↩
The attacker doesn’t even have to be an expert hacker to do this. For $10, you can get a very good book explaining how to do it. ↩